No key, mo problems
When there's no attacker to blame
The other day 14 year olds visited the office for a 2-day internship. They knew nothing of blockchain, so I explained:
— If you lose a website password what do you do?
— Uh, just reset it.
— Imagine you can’t reset it. And it’s a site where you store money, so without the password the money’s gone. Would you use that?
— What? No, that’s insane.
— It’s called blockchain.
Lost your key, lost you coins.
Today I’ll walk you through a few real cases of key loss, not only blockchain wallets. Then I’ll share practical advice that goes beyond “do backups.”
Key loss examples
Just a few cases for different types of keys.
Bitcoin wallets: $xxB
Everybody knows the story of the 8000 BTC hard drive buried in a landfill back in 2013. Millions of bitcoins are gone forever due to lost keys, dead owners, or dust UTXOs.
Every day, an average of 231 BTC are irreversibly lost due to lost keys or failed backups, and 81% of crypto users once lost access to a wallet. These figures aren’t true, but the real ones are probably worse. People and companies hide these things.
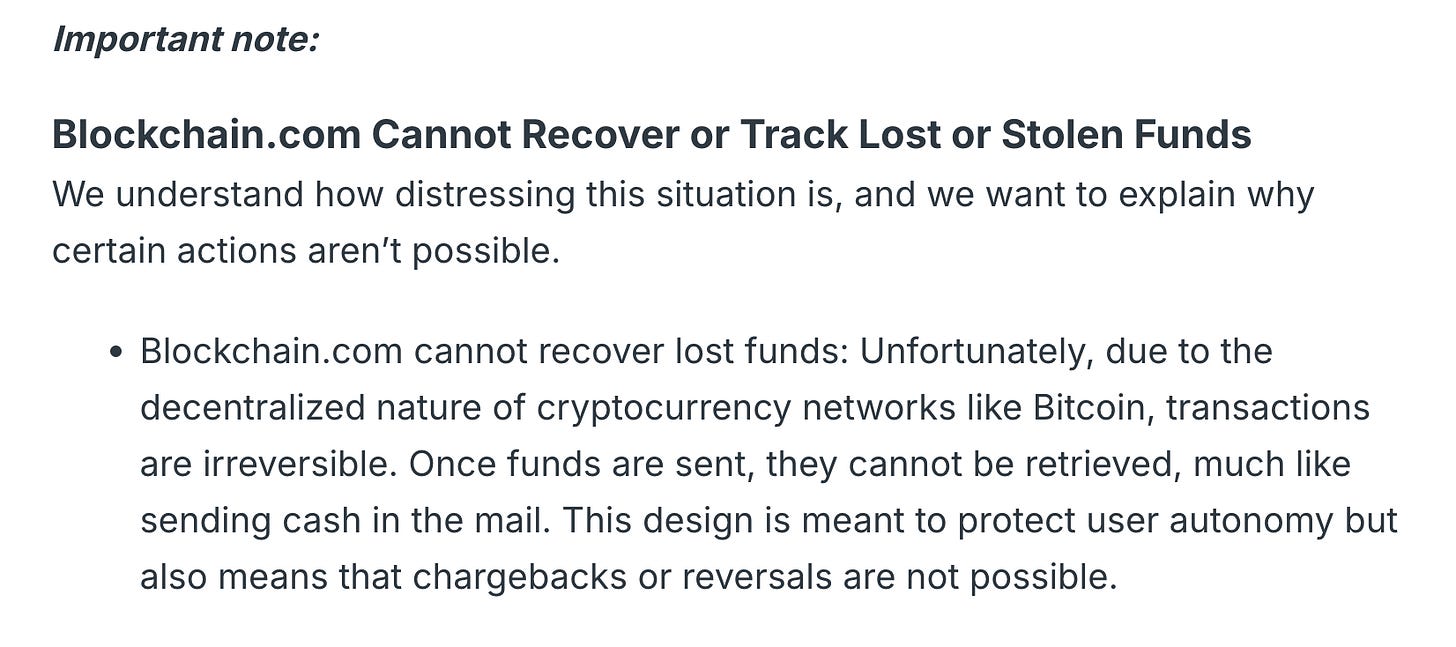
Plenty of companies sell “wallet recovery services,” but if you lost your seed phrase, mnemonic, or private key, your coins are gone, unless you used a shitty wallet with poor entropy, in which case you have a different problem.
Blockchain.com says it clearly:
“Much like sending cash in the mail.” Yeah, but nobody ever claimed mailing cash was the future of finance.
StakeHound MPC share: $75M
In 2021, Swiss company StakeHound lost access to (then) $75M worth of ETH because they failed to back up the BLS they generated for their Eth beacon node. The key consisted in threshold signing shares, produced following Fireblocks’ instructions. The instructions also said “create backups”, but this part was ignored. StakeHound blamed Fireblocks anyway.
NGO database decryption key
Years ago, a large NGO in Switzerland experienced database corruption that wiped part of their DB. The IT and security guys didn’t panic: “let’s restore from the last backup, the RPO is 24 hours, no biggie.”
Then they fetched the backup from cold storage and discovered it was encrypted. And nobody knew how to decrypt it. The engineer who wrote the encryption tool had left the company, they didn’t find the decryption tool, let alone the private RSA key needed to unwrap the symmetric encryption key.
They never recovered the data.
Cold water storage
This private certificate authority took security seriously: the CA root key was on a hardware token, and backup in another. Two YubiKeys, both on the CISO’s keyring.
One day the CISO felt unwell and went for a boat ride on Lake Geneva. He sat on the gunwale to enjoy the sunset, and the whole keyring slipped into the lake. YubiKeys are waterproof, but defense in depth doesn’t mean drop them down a lake.
But it was compliant
This organization used HSMs to store signing keys and decryption keys. They followed their backup policy: “Private keys must be backed up on FIPS-compliant, encrypted USB drives.“
What the policy didn’t say was “distinct USB drives.” All the signing keys, SSH keys, PGP keys ended up on the same single USB drive, stored safely in a bank safe.
When the HSM died, they fetched the USB drive, got the decryption passphrase, but… the stick was unreadable. And of course, there was no backup of the backup.
IACR elections decryption key
The International Association of Cryptography Research runs votes for directors elections and other matters using Helios, an online voting application offering:
Privacy: Voters’ choices are not visible to the organizers (although they could in principle decrypted, more on that later).
Verifiability: Voters can verify that their vote was taken into account in the final tally.
Helios uses homomorphic encryption to combine the encrypted ballots into an encrypted tally. To decrypt it, three trustees must participate in the decryption process, each using their private key. This isn’t threshold decryption, but “homomorphic decryption” using ElGamal (see details).
After the last election that ran until November 16, IACR realized one trustee had “irretrievably lost their private key” (quoting from an email sent to IACR members). So the tally can’t be decrypted, and IACR must rerun the election.
Advice
My humble advice:
No key, no problem
Don’t manage keys yourself unless you must. Don’t use cryptography just to feel clever. Key generation, rotation, usage, storage, recovery; you only need to get one step wrong to lose everything.
Don’t manage keys yourself if you can avoid it. Don’t use cryptography just to feel clever. Key management is hard: generation, storage, rotation, storage, recovery. Think about:
What's the risk of that cryptocurrency exchange going belly up vs. the risk of losing your self-custodied key?
Do you really need two levels of encryption using keys Shamir-shared in hardware tokens for the family photos on your private NAS? Maybe availability matters more than confidentiality.
Good security isn’t paranoia, it’s good risk modeling.
Backups
Doing backups is easy, managing backups is hard. Think about:
What media: USB drive, cloud drive, paper note, CD-ROM?
What to copy: One key on one device? Multiple copies? Shamir-split shards?
Where to store: A drawer at home? A bank safe? Under your mattress?
How to remember recovery instructions and backup locations?
How to test: Optimism isn’t a strategy, check that the backups work and that you backed up the right thing. Set reminders for that.
Featured image: Memento.